Review: Attacking and Defending Active Directory
Posted on June 18, 2020 in Cybersecurity
Today I have finished the Attacking and Defending Active Directory course by passing the CRTP examination. At the moment, this course is relatively unknown. This is why I decided to write a review about it, since I really like the course. As its title already says, all the basics about attacking Active Directory environments is tought and how to mitigate those attacks as well.
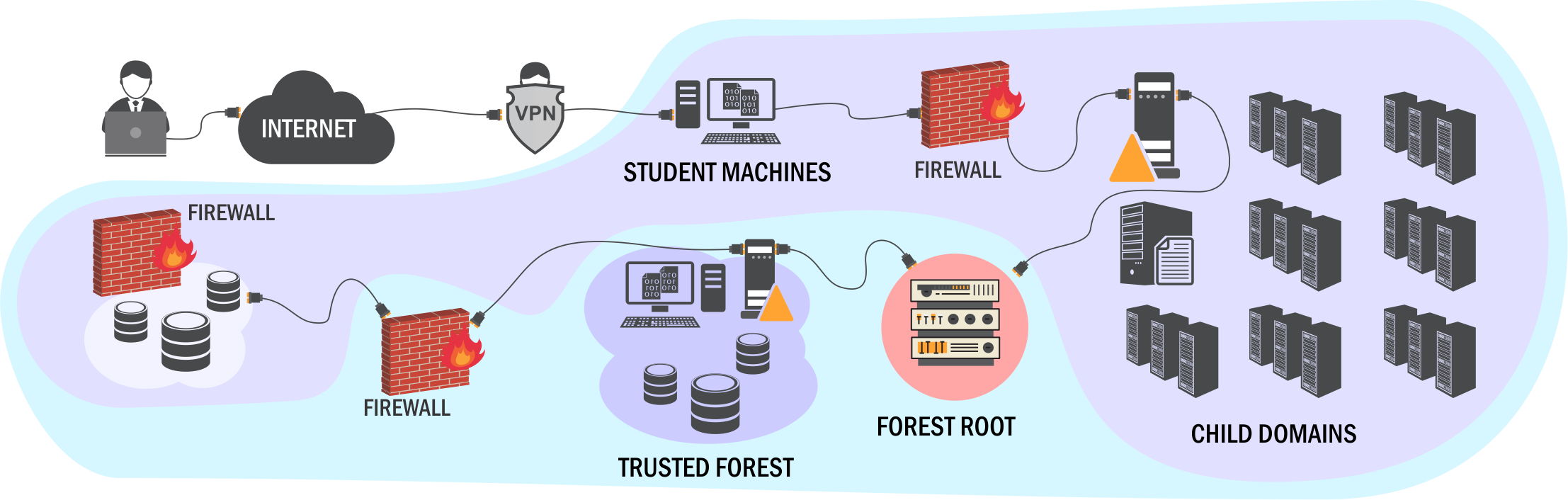 Source: pentesteracademy.com/activedirectorylab
Source: pentesteracademy.com/activedirectorylab
Lessons Learned
Before I started the course, I already had knowledge in penetration testing and of course I did local privilege escalation on Windows systems many times, e.g., on HackTheBox. However, abusing common misconfigurations in an Active Directory was new to me for the most part. I took especially two things from the course that I experienced in the labs:
- If a single Domain Administrator gets compromised, the trust of the entire forest is at risk
- If a Domain Controller gets compromised, it is almost impossible to sanitize the DC without completely reinstalling the entire DC
This applies for every Active Directory as forests are the only trust boundary. Persistence, i.e. remaining access on the compromised DC, is easy and there are a lot of techniques available.
Course Materials
The course materials and the lab are highly integrated. That means, you can basically follow the steps in the PDF document or watch the videos to compromise the whole lab environment. But you are encouraged to find attack paths by yourself and try out tools that are not covered in the course. The course materials mainly consists of 36 videos that cover one topic per video. The videos are about 20-30 minutes each and conclude with a practical exercise. This is where my only criticism comes in. Sometimes, the instructor doesn't get to the point and the video could be a few minutes less.
The lab is tightly integrated with the course and is designed as a practice lab rather than a challenge lab. We cover topics like AD enumeration, trusts mapping, domain privilege escalation, domain persistence, Kerberos based attacks (Golden ticket, Silver ticket and more), ACL issues, SQL server trusts, Defenses and bypasses of defenses.
As I mentioned, you learn all the bascis about attacking Active Directory. In my opinion, the most value resides in the defense part. I didn't find too many useful free blog posts about this topic and you also get an idea how experienced the instructor actually is. Besides the course materials you pay in particular for accessing the lab environment, which means a practical hands-on experience. And I think blogs are no substitute for getting practical experience.
The Lab
The lab is a shared enviroment which is also accessed by other students via VPN. You can also use your web browser to access your machine via RDP via Guacamole which is really cool! The servers are regularly reset on a daily basis to keep a fresh state. Your own student machine is never reset by default. But you can ask the support team to reset your machine. Typically, the support team has an excellent response time (only a few minutes) and they are very kind.
The lab environment is comparable to a small and medium-sized enterprises' Active Directory in terms of size. There are a few desktop machines, several servers running different services and configurations in multiple domains (even multiple forests). The intended misconfigurations are fairly realistic in my opinion and the attack path to compromise the whole forest is well thought out. At least, you can learn many concepts and all the fundamentals. No crazy advanced techniques are used. But you are tought to bypass 'normal' security features like Windows Defender or AMSI. As the machines are all on the latest patch level, using exploits is not part of the course.
If you're not sure how many days in the lab you should purchase, I can tell you that I finished the complete lab in 14 days. You can also expand your lab access period later on. Be aware that exam slots are limited. So schedule your exam in good time prior your lab access ends.
The Exam
The examination is structured similar to the OSCP. You get VPN access to a domain computer in an unknown Active Directory environment. So you don't need a Kali VM or any other preparation. It is important to know that there are no tools preinstalled on the host you have unprivileged access to, initially. This is why you have to know your toolset and you must be able to install all the tools that are covered in the labs. In order to successfully pass the exam, several systems has to be compromised within 24 hours and you have to write a detailled report. If you cannot compromise all the hosts, it is still possible to pass the exam if your report is excellent. The certificate requires re-certification after 3 years.
A few words about how to connect to the exam: the connection to the initial RDP host was stable and the system wasn't slow. If you want to connect to the exam using your web browser, I can recommend using Google Chrome browser. There is no proctoring, however, I discovered tracking of your PowerShell history in log files.
My exam didn't go very well at the beginning. I was able to get access on the first host within 2 hours. Honestly, that wasn't too easy but doable. But then I was stuck for hours and hours on the second host. In retroperspective, I just didn't enumerate the Active Directory good enough. I actually learned something while being in the exam situation ;) This is something I already mentioned: know your tools! Don't always rely on the output of one individual tool. I got tons of false-positives. After compromising the first two machines, I get the other machines relatively quickly. To sum up, the beginning is not easy, but the difficulty level gets gradually easier after every box you have compromised.